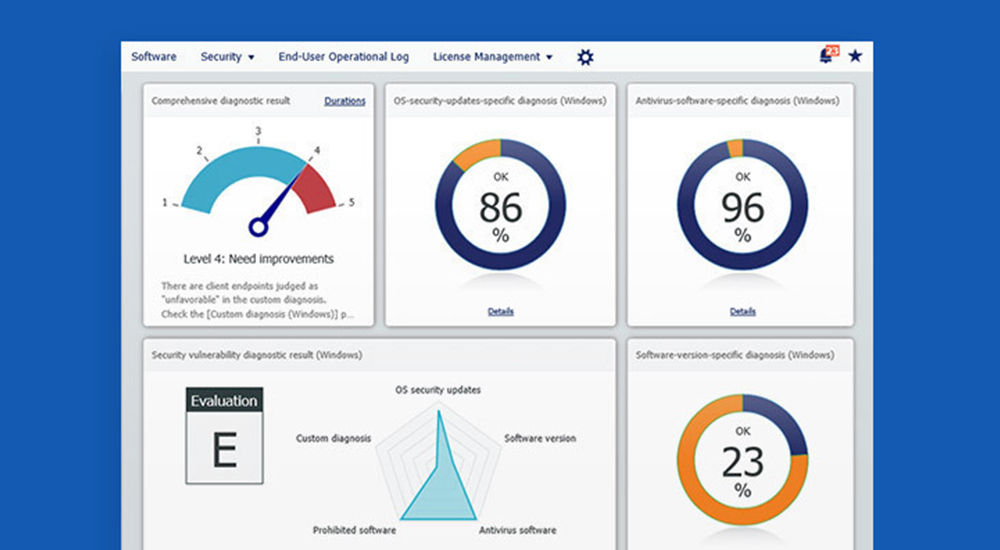
As IT is increasingly used in business, so is there an increase in the number of cyberattacks and the damage they cause.
Meanwhile, confidential information related to corporate business and the personal information of customers are being shifted to data-based management.
While such data management is convenient, as long as a computer is connected to the Internet, there is a risk of being attacked from the outside.
To protect against the theft of your confidential data, robust protection is essential.
Security has become one of the most important issues facing company managers.
Leave it to KDDI America

We know we need better security, but we don't know where to start.

We want to strengthen security, but we don't have enough human resources.

We want security that suits hybrid work styles.

We want to know where our company's security is lacking.

We want to know about Zero Trust
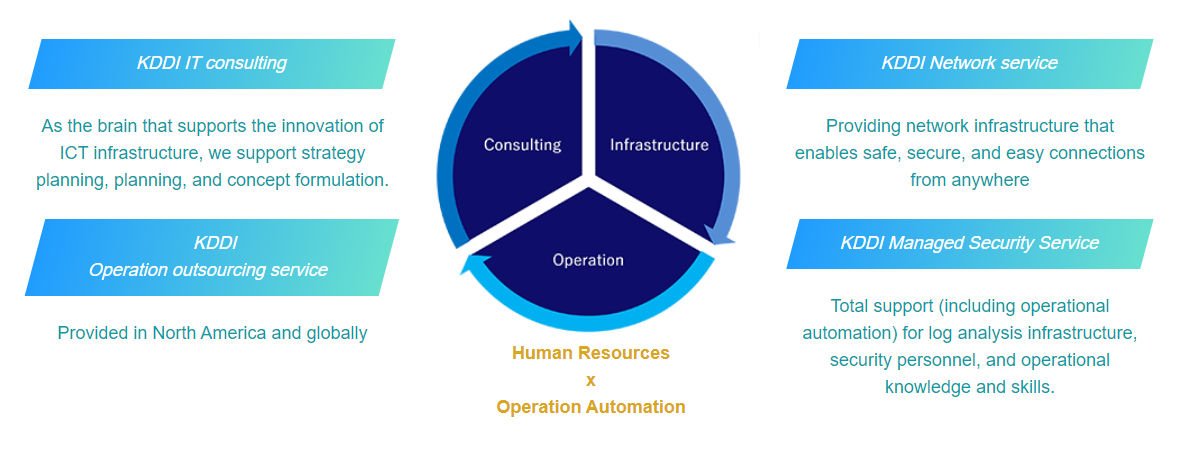
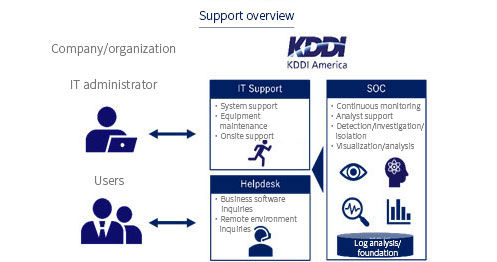
Building efficient and consistently high-quality system infrastructures
One-stop provision of design, construction, introduction, and operation for various systems
Intelligence cycle for building, operating and planning an ideal IT environment
Greatly reduce work load by fully outsourcing infrastructure, operation, and concept planning
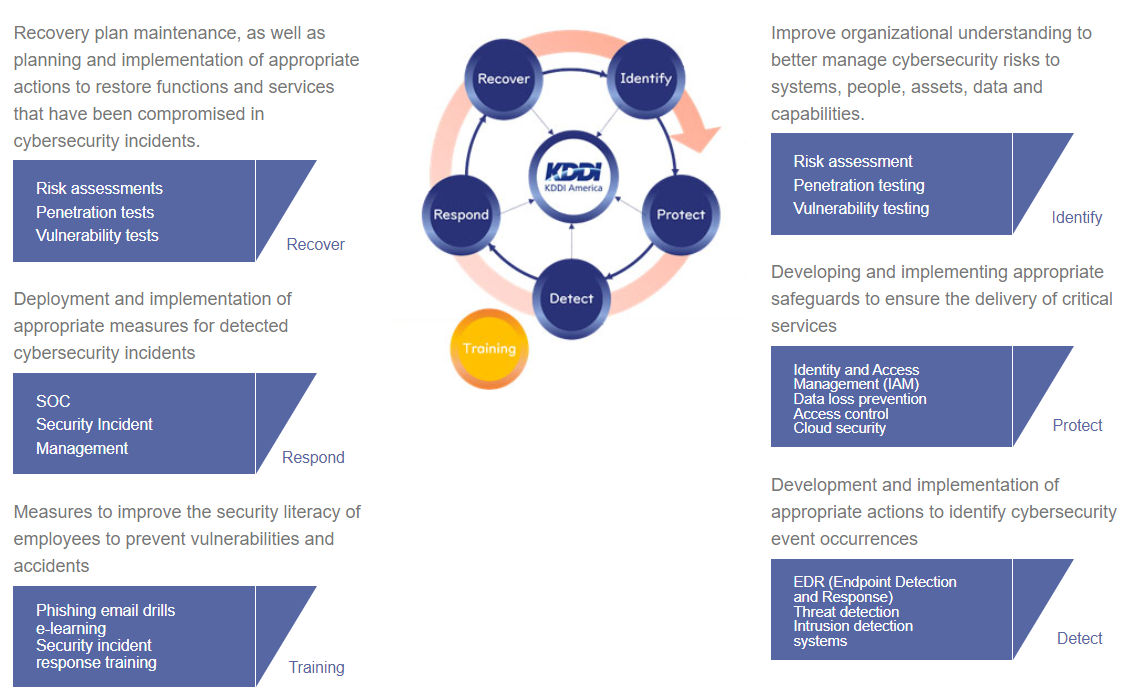
One-stop solutions for security issues at overseas offices
Ideal for strengthening global security governance
We provide a comprehensive range of services that address the five items required for security measures as defined by the cybersecurity framework issued by the National Institute of Standards and Technology (NIST).
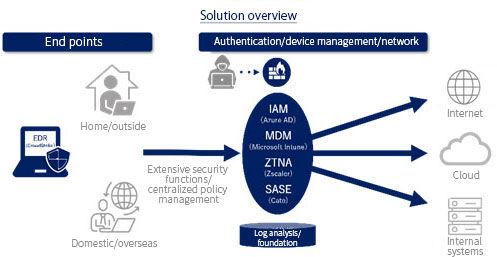
Let KDDI America guide you to Zero Trust solutions that support diversifying work styles.

KDDI America Zero Trust Solutions: Two major features
Feature1
All-in-one provision of the complex functions required in a changing environment
We provide comprehensive solutions covering issues such as user access/privilege management (IAM*1), secure access implementation (ZTNA*2/SASE*3), endpoint device management functions (MDM*4) and endpoint security measures (EDR*5)/monitoring.
Feature2
Outsourcing for a wide range of management and operation issues
In order to better fit today's distributed work environment, we have expanded our support system to meet the needs of each user, not just the your IT staff, contributing to improved operational efficiency by reducing the burden on your customer representatives
Learn more about Zero Trust solutions here
Why customers choose KDDI America

All-in-one offerings
We provide end-to-end services for security ranging from infrastructure construction to operation to user support
Strengthened security governance
We enable you to strengthen your global security governance through cooperation between regions
Line up



Related White Papers
Steps to introducing zero trust for global companies

Key Points for Security Measures at Overseas Locations

Related Knowledge Articles







Related Case Study


What is the best solution for your problem?
Please consult a KDDI consultant.